In this video I show how to use the brute forcer hydra.Here is the direct link to download the windows package of thc-hydra:http://freeworld.thc.org/thc-hydr. Downloading and Installing HYDRA For Windows Users Important note: before installing this version, be sure to uninstall the previous one! Using: Start-Control Panel-Add/Remove Programs. Download the installer file from this location to a temporary directory. When the transfer is complete, just run this file and follow the instructions.
Hey Folks, in this tutorial we are going to discuss about another tool called “X-Hydra“. Basically it is a GUI version of the Hydra bruteforcing tool and if you want to know about its command line tool you can go here. Apart from this you can read the complete introduction of this tool by visiting our previous article.
Let’s take a look 🙂 !!
X-Hydra
As we told you this is the GUI version of the Hydra tool that we can boot using the following command.
Basic Brute force Attack
In this attempt we will use dictionary for getting the correct login details. In the targets tab, we will fill single host, port and protocol details and move towards the password section.
Now here we have to give the location of both username and password dictionary files. You can make an powerful dictionary from here.
Just we go to the “start” tab and click on the start button. As you can see that after hitting the start button we got 2 valid credentials.
Bruteforce on Forward Port
Sometimes the administrator changes the port number to give additional protection to the running services. As you can see that now the FTP service is running on port 2121.
Now we need to change the port number instead of service.
Done 🙂 !! As you can see it worked and even it gave us valid credentials.
Verbose Mode
By enabling both of these features we can see deeper details of the ongoing brute force attack.
Nice 🙂 !! The results are in front of you and we can clearly see that which user and password combination it’s using to get the right credentials.
Guessing Passwords
Now we will use the specific user and try to find the correct credential using the password word list.
Great 🙂 !! It successfully finds the correct login details without using more combinations.
Combo
Now we will put both username and password in a file and separate them from each other using colon. We will then select the file location where we created the file.
Nice 🙂 !! Finally it has got a valid username and password.
Multiple Hosts
All you have to do is create a list of hosts and submit the location of that file on target list option.
Done 🙂 !! Likewise we can get better results by using all these features of this tool.
A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.
Step By Step Online Password Bruteforce With THC Hydra
Hydra (better known as “thc-hydra”) is an online password attack tool. It brute forces various combinations on live services like telnet, ssh, http, https, smb, snmp, smtp etc. Hydra supports 30+ protocols including their SSL enabled ones. It brute forces on services we specify by using user-lists & wordlists.
Hydra works in 4 modes :
- One username & one password
- User-list & One password
- One username & Password list
- User-list & Password list
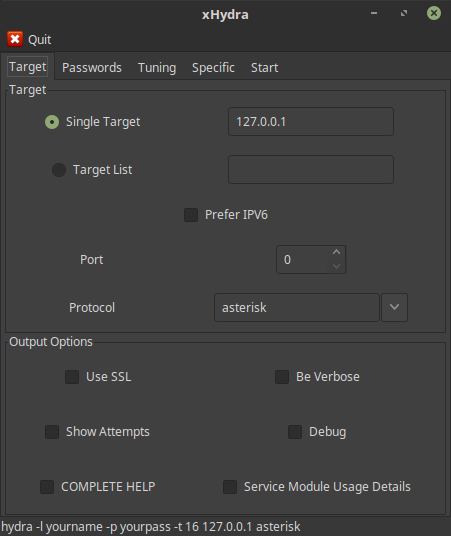
Pentesters use this tool to test/audit the password complexity of live services mostly where direct sniffing is not possible. We discuss the gui of the tool in the following tutorial. In future, the command line mode will be discussed.
You can open xHydra from the Kali linux menu or terminal.
- Target - Settings of various target oprions.
- Passwords – Specify password options & wordlists.
- Tuning – Secify how fast should hydra work. Other timing options are also available.
- Specific – For testing on specific targets like a domain, https proxy etc.
- Start – Start/Stop & shows the output.
Breaking an ssh with wordlist attack – Hydra
In this lab we try to break an ssh authentication on a remote has who has IP address 192.168.0.103. Here we do a wordlist attack by using a wordlist containing most common passwords to break into the root account.
Step 1 :
Open thc-hydra
Step 2 :
Thc Hydra Gui For Windows 10
Set Target & protocol in the target tab.
Step 3 :
Set the username as root & specify the location for a wordlist in passwords tab.
Note : Kali Linux comes with built-in wordlists. Search them using the command : locate *.lst in terminal.
Other wide ranges of wordlist ranging up to 3GB or more are available on the internet. Just google for 5 minutes.
Step 4 :
Set no of tasks to 1 in tuning tab since this will reduce congestion & chance of detection. But takes longer to complete. This is also necessary to mitigate account lockout duration.
Step 5 :
Start the thc-hydra from Start tab.
Step 6 :
Scroll Down & Wait until the password gets cracked
- THC Hydra is easy-to-use, user-friendly tool
- Includes a GUI for those that do not know how to work with the cmd.
- Hydra is ideal for brute force and dictionary password cracks of over 30 different protocols.
- Other common remote authentication tools are Medusa and Ncrack.
- These perform similar functions as THC Hydra and can also be downloaded online.
Thc Hydra Gui For Windows 9
- Speed comparisons reveal that all three tools are relatively similar in output times.
- Hydra top-ranking because of so many supported protocols.
Thc Hydra Gui For Windows 7
- THC Hydra is a great option for performing a brute force/dictionary
- crack of a remote authentication service.